Introduction
Sensitive data processing and storage has expanded dramatically as a result of industry’ fast digital transformation. Safeguarding access to data assets, such as intellectual property and personal information, is crucial. The ideas of permission and authentication are essential for maintaining security, defending resources, and preserving private data. Despite their frequent interchangeability, the two phrases refer to different procedures in access control systems. Building strong security architectures requires an understanding of the variations and best practices pertaining to these procedures.
The complexities of authorization and authentication are examined in this essay, along with their functions in contemporary security systems, cutting-edge technologies, and creative methods of protecting digital spaces. We will look at how these ideas are used in various sectors, how authentication techniques have changed over time, and the effects of emerging technologies including biometrics, decentralized authentication, and multi-factor authentication (MFA).
1. The Basics of Authentication and Authorization
1.1 Defining Authentication
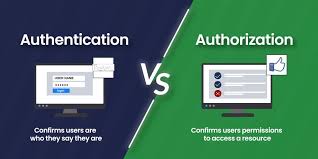
The process of confirming a user, device, or system’s identity is known as authentication. In any access control system, it serves as the initial line of defense. Authentication, to put it simply, provides an answer to the inquiry, “Who are you?”
Providing credentials, such as a password, token, biometric information, or cryptographic key, is usually required for authentication. The identity is confirmed and access to protected resources is allowed if the credentials match the data in the system’s database.
Three main categories of authentication exist:
Something you are aware of: a secret, usually a PIN or password.
Something you own: A tangible item, such a hardware token, smartphone, or smart card.
Something that you are: a biometric trait, like an iris scan, fingerprint, or facial recognition.
1.2 Defining Authorization
Following the authentication of a user’s identification, the system has to decide which resources and actions the user is authorized to access. The process of allowing or refusing access to particular resources in accordance with the roles or permissions of the authenticated user is known as authorization.
Access control policies, which specify what a user can do after authenticating, are commonly used in authorization. These regulations may be founded on things like:
- Role-Based Access Control (RBAC): Permissions given according to a user’s function within an organization are known as role-based access control, or RBAC.
- Attribute-Based Access Control (ABAC): Permissions based on user qualities, such department, location, or security clearance, are known as attribute-based access control, or ABAC.
- Discretionary Access Control (DAC): Access permissions given at the resource owner’s discretion are known as discretionary access control, or DAC.
By guaranteeing that users can only access the resources required for their task, authorization aims to reduce the attack surface by upholding the principle of least privilege.
2. The Relationship Between Authentication and Authorization
Authorization and authentication are two different but closely connected processes. Authorization establishes what the user is permitted to do, whereas authentication confirms the user’s identity. Since sensitive resources could be accessed by unauthorized users in the absence of authentication, both are crucial for safeguarding digital systems. Similar to this, authenticated users may access resources or take actions they are not permitted to take if they are not properly authorized.
For example, in a corporate setting, an employee may be granted access to specific files or systems according on their work position after authenticating with a password (authorization). Similarly, a nurse would only be able to see certain data, whereas a doctor might be able to examine patient records after authenticating with a fingerprint scan.
Authorization comes after authentication in the majority of security setups. Authorization is meaningless in that situation since a user who fails authentication is not allowed to access the system at all.
3. Traditional Authentication Methods
3.1 Password-Based Authentication
The most popular type of authentication in the past has been password-based. Users must generate a secret character string, which the system stores and is frequently hashed for security. However, there are a number of disadvantages to password-based authentication:
Weak Passwords: Accounts are at risk because users frequently select simple passwords like “123456” or “password.”
Password Reuse: When users reuse their passwords on different platforms, the likelihood of one platform being compromised increases.
Phishing: By using social engineering or phony websites, attackers might fool users into divulging their credentials.
Multi-factor authentication (MFA) was created to counteract these flaws. FA) was introduced.
3.2 Multi-Factor Authentication (MFA)
Before allowing access to a system, MFA requires users to present two or more forms of identity. Users may be required, for instance, to input a code that is texted to their phone (something they have) and a password (something they know).
By making it more difficult for attackers to obtain illegal access, even if they have compromised one type of authentication, MFA offers an extra layer of security. Typical MFA techniques include:
- Codes based on email or SMS
- Apps for authenticators (like Authy and Google Authenticator)
- Push alerts
- Hardware tokens, such as the YubiKey
MFA greatly increases the authentication process by integrating many elements, making it more difficult for attackers to get around.
3.3 Biometric Authentication
Unique bodily traits are used in biometric authentication to confirm a user’s identification. Because biometrics are harder to copy or steal, they are thought to be more secure than passwords. Typical biometric techniques consist of:
- Recognition of Fingerprints
- Recognition of faces
- Recognition of Voices
- Iris scans
- Verification of palm veins
Although biometric authentication can offer a high degree of security, there are drawbacks, including the possibility of false positives or negatives, privacy issues, and system integration problems.
3.4 Single Sign-On (SSO)
Users may authenticate once and access numerous apps or services without having to log in repeatedly thanks to Single Sign-On (SSO). By minimizing the amount of authentication prompts, SSO improves user experience. In business settings where users must access a range of systems and services, it is frequently utilized.
Federationed authentication is frequently implemented using SSO systems such as OAuth, SAML, and OpenID Connect. SSO allows users to access multiple service providers (SPs) without requiring extra login attempts after authenticating through an identity provider (IdP).
4. Authorization Methods and Techniques
4.1 Role-Based Access Control (RBAC)
RBAC is one of the most commonly utilized authorization models. RBAC assigns rights based on the user’s function within an organization. Roles are often created based on job functions, and users are given access to resources that are relevant to their role.
For example:
A Sales Manager may be given access to CRM data and reports.
System Administrators may have access to server configurations and user management tools.
RBAC simplifies access permission management by allowing roles to be quickly amended or updated to reflect changes in an organization’s structure..
4.2 Attribute-Based Access Control (ABAC)
Attribute-Based Access Control (ABAC) is a more flexible and dynamic authorization paradigm than RBAC. ABAC grants access based on a set of attributes (or qualities) relating to the user, resource, and environment. These traits could include:
- User attributes include department, security clearance, and job title.
- Resource features include data sensitivity, classification, and location.
- Environmental characteristics include time of day, device kind, and IP address.
ABAC enables for more detailed access control by making judgments based on various attributes. For example, an employee may only be permitted access to particular papers if they are connected to the corporate network and logged in during business hours.
4.3 Policy-Based Access Control (PBAC)
Policy-Based Access Control (PBAC) is a more recent and evolving approach that expands on ABAC. PBAC employs policies specified by organizations to decide access using a set of rules. These policies are frequently highly personalized and context-sensitive, allowing for more sophisticated decision-making.
For example, a company may have a policy indicating that only users with the “Manager” attribute in a given department have access to certain financial records at specific periods of the year.
4.4 Discretionary Access Control (DAC)
Discretionary Access Control (DAC) is a less restricted model in which the owner of a resource (such as a file or database) decides who has access. In DAC, users can grant or refuse access to other users at their discretion.
While DAC provides flexibility, it is frequently regarded as less secure than other models because it relies on individual users to maintain access permissions.
5. Challenges in Authentication and Authorization
While authentication and authorization are vital to security, some difficulties remain.
5.1 Balancing Security and User Experience
he usage of robust authentication and permission procedures frequently causes difficulty for users. For example, multi-factor authentication can improve security but can also cause user aggravation if not properly implemented. Finding the correct balance between security and user ease is critical for preserving productivity while protecting against threats.
5.2 Phishing and Social Engineering Attacks
Even the most secure authentication techniques can be compromised by phishing and social engineering attempts. Users may be duped into disclosing their credentials or granting illegal access, emphasizing the significance of user awareness training in cybersecurity.
5.3 Privacy Concerns in Biometric Authentication
While biometric authentication provides high security, it also presents privacy and data protection concerns. Biometric information is extremely intimate and difficult to change if hacked. It is vital to ensure that biometric data is securely stored while also adhering to privacy requirements like GDPR.
5.4 Managing Access in Complex, Distributed Systems
As enterprises use cloud computing, microservices, and distributed systems, handling authentication and authorization becomes more difficult. Multi-cloud setups, hybrid infrastructures, and third-party interfaces necessitate careful attention to identity federation, secure API access, and uniform access control procedures.
6. Future Trends in Authentication and Authorization
6.1 Decentralized Identity and Blockchain
Blockchain and decentralized identity systems are emerging technologies that have the potential to change authentication and permission. Decentralized identity systems provide users authority over their own identities and access credentials, decreasing dependency on centralized identity suppliers. Blockchain technology can help maintain data integrity and prevent illegal access to sensitive personal information.
6.2 AI and Machine Learning for Authentication
AI and machine learning are being used in authentication systems to detect anomalies and improve decision-making. Behavioral biometrics and risk-based authentication employ machine learning algorithms to detect suspect activities based on trends in user behavior (for example, typing speed, mouse movement, or login location).
6.3 Continuous Authentication
Rather than relying exclusively on one-time authentication during login, continuous authentication entails confirming users’ identities throughout their session depending on their behavior and the surroundings. This strategy lowers the likelihood of unwanted access if a session is hijacked or a user leaves their device alone.
Conclusion
Authentication and authorization are critical components of modern cybersecurity, ensuring that only authorized users have access to sensitive resources and protecting digital environments from illegal invasions. As security threats grow and new technologies emerge, organizations must constantly modify their authentication and authorization strategies, employing cutting-edge solutions like multi-factor authentication, biometrics, and blockchain.
In the face of growing complexity and security threats, a layered approach to authentication and authorization, together with user awareness and strong policies, is critical for ensuring the integrity and security of digital systems.
Relevance Article:
https://alphalearning.online/end-to-end-development-a-comprehensive-overview-and-future-innovations
External Resources:
https://www.onelogin.com/learn/authentication-vs-authorization

Leave a Reply